![[EdCert previous]](../../edcert/images/prev.gif)
![[EdCert next]](../../edcert/images/next.gif)
![[EdCert top]](../../edcert/images/top.gif)
Okay. Let's say there is a workstation, Dinky, that's on the desk of a user named Ramona who works in the shipping and receiving department of Widget Works. In the top floor executive suite of Widget Works is a workstation, Gargantuan, that has all sort of important documents on it including a list of who is going to get a raise next month.
Ramona wants to know is she's going to get a raise, but only the top executives at Widget Works and the system administrator have accounts on Gargantuan. So she can't log directly into Gargantuan. Ramona does a lot of work with the Accounting department, including writing scripts to help keep track of which shipments have been sent where. Ramona has root privileges on Dinky and Dinky is in the /.rhosts file for one of the workstations in Accounting, Adderup.
Because Adderup is used to archive purchase information it is in the /.rhosts file for picky, one of the machines in Purchasing. Well the Chairman of the Business Office needs access to the information that machine so Picky is in the /.rhosts file for his machine, Big. And Big is in the /.rhosts file on Bigger, a workstation used by the Vice Presidents at Widget Works. There is another machine, Muchbigger, all the Executive Vice Presidents have access to and Bigger is in it's /.rhosts file. And finally Muchbigger is in the /.rhosts file for Gargantuan as the same system administrator takes care of both machines.
So if Ramona takes advantage of Dinky being in the /.rhosts file on Adderup, then uses the /.rhosts entry for Adderup on Picky to gain root privileges on Picky, and keeps going....
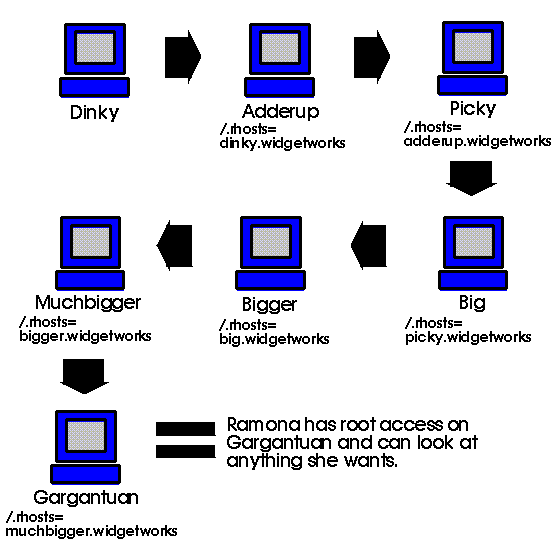
Eventually Ramona will be logged into Gargantuan as root, because the /.rhosts entry allows a user to log in as anyone they want.