| Previous | Table of Contents | Next |
Multiple static defaults can be used at the same time. One way to set multiple static defaults is to point to multiple networks (use aggregates if possible for stability reasons) and establish a degree of preference by using the local preference attribute. This would apply to a single router connected to the provider via multiple connections, or multiple routers running IBGP inside the AS. Both scenarios are illustrated in figure 6-5. These are similar to the scenarios you saw in figure 6-2, the only difference being that the customer is setting its own default rather than relying on the provider to send the 0/0 default route. In this example, the customer will choose 128.213.0.0/16 with the local preference of 100 via the upper link. The lower link will be used as backup in case of failure in the primary link.
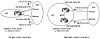
Figure 6-5 Statically pointing to multiple networks defaults.
Another way of setting defaults statically involves using the Cisco distance parameter (as described in Chapter 5, "Tuning BGP Capabilities," table 5-1) to establish a degree of preference. This would work only in the case of one router connected to multiple connections because the distance parameter is not exchanged between routers.
If two static default entries are defined with different distances, the default with the lowest distance wins. If the better default goes away, the second default becomes available. If both defaults have the same distance, then traffic will be balanced between the two defaults.
Figure 6-6 illustrates the use of the distance parameter in setting multiple defaults. AS1 is connected to AS2 via two links and is setting its own defaults toward AS2. AS1 uses one link as primary by giving the static default a distance of 50, lower than the distance of 60 given to the backup link. In case of failure in the primary link, traffic will shift toward the backup.
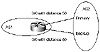
Figure 6-6 Static defaults pointing to multiple connections.
Symmetry
Symmetry refers to the fact that traffic leaving the AS from an exit point comes back through the same point. This is easy to achieve if a single exit and entrance point exists. But, given the mandates of redundancy and the presence of multiple connections, traffic tends to be asymmetrical. When it is, customers and providers notice a lack of control over how traffic flows in and out of their ASs. Traffic leaving the AS from the East Coast might end up taking the "scenic route," coming back from the West Coast and traveling inside the AS multiple hops before returning to its origin.
Actually this is not as bad as it sounds, and in some situations asymmetrical traffic is acceptable depending on the overall physical topology as far as the speed of the links and the number of hops between locations. In general, customers and providers would like to see their traffic come back close to or at the same point it left the AS to minimize potential delays that could be incurred otherwise.
To accommodate symmetry, a primary link should be chosen, and a best effort should be made to enable the majority of traffic to flow on this link. Redundancy would be accommodated by enabling other links to be backup links that will be used if the primary link is problematic.
Load Balancing
Load balancing deals with the capability to divide data traffic over multiple connections. A common misconception about balancing is that it means an equal distribution of the load. Perfectly equal distribution of traffic is elusive enough even in situations where traffic flows in a network that is under a single administration. Given the multiple players that traffic has to touch, equal distribution of the traffic is difficult to achieve in most scenarios. Load balancing tries to achieve a traffic distribution pattern that will best utilize the multiple links that are providing redundancy. To achieve this requires a good understanding of what traffic you are trying to balance, incoming or outgoing.
It is important not to think about traffic as a single entity. Traffic is two separate entities, inbound and outbound. With respect to an autonomous system, inbound traffic is received from other ASs, whereas outbound traffic is sent to other ASs.
Suppose that you are connected to two ISPs and traffic is overloading your link to ISP1. Your question should be: What traffic—inbound or outbound? Are you receiving all your traffic from ISP1, or are you sending all your traffic toward ISP1?
The patterns of inbound and outbound traffic go hand in hand with the way you advertise your routes and the way you learn routes from other ASs. Inbound traffic is affected by how the AS advertises its networks to the outside world, whereas outbound traffic is affected by the routing updates coming in from outside ASs. Make sure that you fully understand this behavior because it will be the basis of all future discussions. From now on, whenever we talk about taking steps to affect inbound traffic, we are really talking about applying attributes to outbound routing announcements because how our routes are learned by others affects how traffic is routed inbound. Similarly, whenever we talk about taking steps to affect outbound traffic, we are talking about applying attributes to inbound routing announcements, because how our network learns routes affects how outbound traffic is routed.
Figure 6-7 illustrates how inbound and outbound traffic behaves. As you can see, the path for outbound traffic to reach NetA depends on where NetA is learned from. Because NetA is received from both SF and NY, your outbound traffic toward NetA can go via SF or NY.
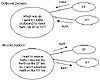
Figure 6-7 Inbound and outbound decisions.
On the other hand, the path for inbound traffic to reach your local networks, NetB and NetC, depends on how you advertise these networks. If you advertise NetC over the NY link only, then incoming traffic toward NetC will take the NY link. Similarly, if you advertise NetB over the SF link only, traffic toward NetB will take the SF link.
| Previous | Table of Contents | Next |